NSDepression
@3ziwib4x8s89088
ID: 1827867560680800258
26-08-2024 00:36:13
146 Tweet
9 Followers
313 Following





Keynote by Halvar Flake at #FUZZING'24 reflecting on the Reasons for the Unreasonable Success of Fuzzing.




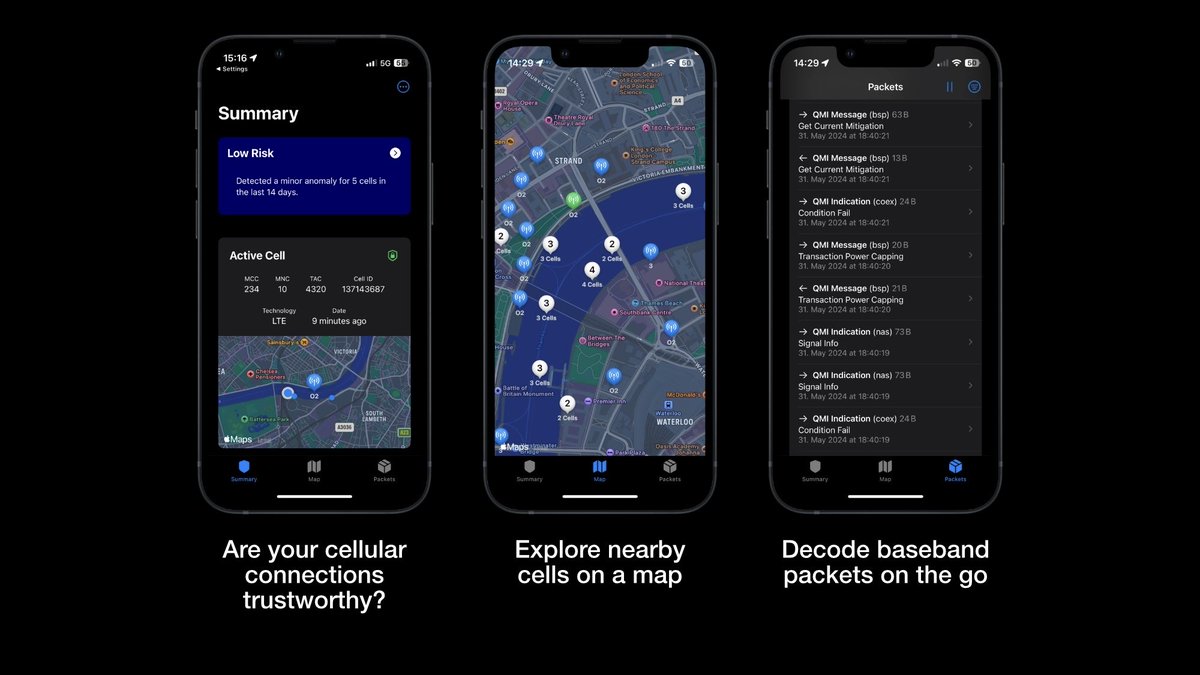
Our paper about the initial research conducted with CellGuard, iOS tooling for Qualcomm basebands, and Apple Location Services has been accpeted for RAID Conference. Read a preprint at lukasarnold.de/posts/raid24-p… x.com/RAID_Conferenc…








Continuing the series on exploiting Android Binder with Binder internals blog androidoffsec.withgoogle.com/posts/binder-i… Deep dive into Binder driver by abcSup and Gulshan. We also release github.com/androidoffsec/… -- tiny lib featuring how to do IPC via Binder driver. Happy Binder hacking!