
Michael Koczwara
@michalkoczwara
Founder @Intel_Ops_io
Threat Intelligence, Adversary Infrastructure Hunting, Curated TI Feed (Coming Soon)
intel-ops.io
medium.com/@Intel_Ops
ID: 133224082
https://academy.intel-ops.io/courses/hunting-adversary-infra 15-04-2010 09:32:35
7,7K Tweet
19,19K Followers
1,1K Following




🚨 Hunt Alert 🚨 Pivoted from the #SlowTempest #IOCs and uncovered a peculiar HTML page—only ~140 results globally, mainly in Hong Kong/China 🇭🇰🇨🇳. Most common port: 8888, potentially a admin/login panel. Thanks Michael Koczwara for your input! Notably, the HTML page pivots

Remember when Moonlock Lab posted about test attempts for a loader targeting #AMOS? I've come across a few samples with low detection rates (ESET, Google, Ikarus). This loader also uses curl to fetch a #macOS #stealer from http[:]//41[.]216[.]183[.]214/
![Xiu (@osint_barbie) on Twitter photo Remember when <a href="/moonlock_lab/">Moonlock Lab</a> posted about test attempts for a loader targeting #AMOS? I've come across a few samples with low detection rates (ESET, Google, Ikarus). This loader also uses curl to fetch a #macOS #stealer from http[:]//41[.]216[.]183[.]214/ Remember when <a href="/moonlock_lab/">Moonlock Lab</a> posted about test attempts for a loader targeting #AMOS? I've come across a few samples with low detection rates (ESET, Google, Ikarus). This loader also uses curl to fetch a #macOS #stealer from http[:]//41[.]216[.]183[.]214/](https://pbs.twimg.com/media/GWlOQtrWgAAlY-2.jpg)




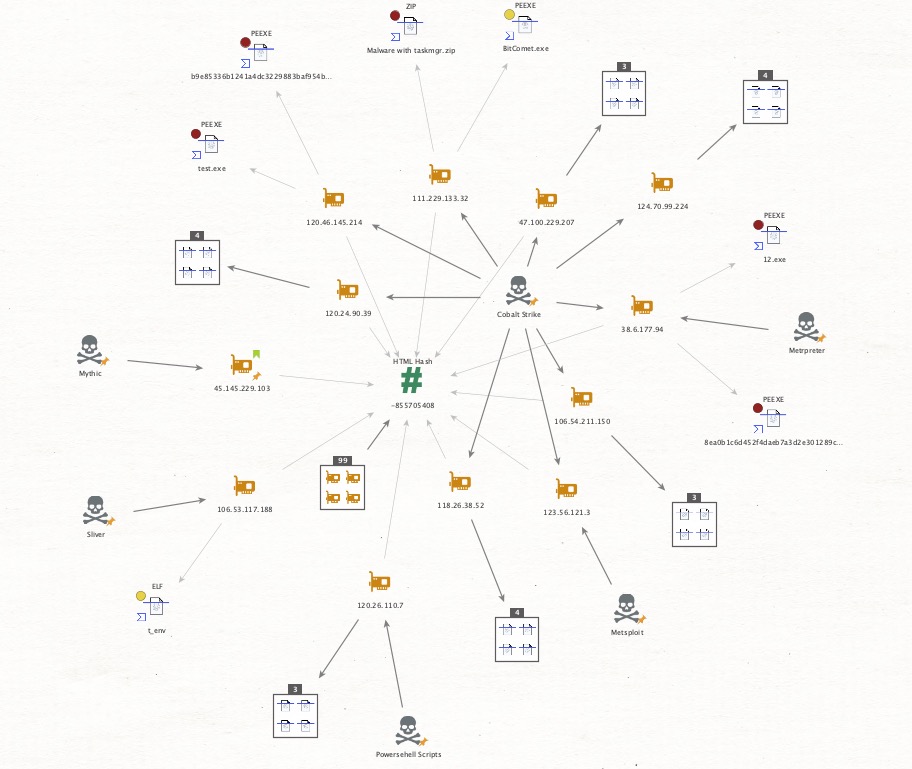
How to use Michael Koczwara's finding below to create a hunting rule in Validin: Banner hash: 4e54378c7ee7ebddee154257ac6bc484 JARM filter: 2ad2ad16d2ad2ad00042d42d00042ddb04deffa1705e2edc44cae1ed24a4da


25 new OPEN, 27 new PRO (25 + 2) SocGholish, Dynamic_DNS, ZPHP, XWORM, Lumma Stealer, VenomRAT, and more Thanks Michael Koczwara community.emergingthreats.net/t/ruleset-upda…




Last week, EclecticIQ published an update on #SCATTEREDSPIDER and provided a few domains used for phishing. Learn how to expand threat intelligence like theirs to find more high-confidence indicators in our latest blog: validin.com/blog/coralling…

🚨 New Blog Post 🚨 Check out my latest analysis on a Stego Campaign using Process Hollowing with .NET injectors! 📜 Full post: somedieyoungzz.github.io/posts/stego-ca… 💡 Learn about the clever use of JS-based droppers, PowerShell scripts, and obfuscated .NET assemblies. 🔗 #Malware #Infosec



![Validin (@validinllc) on Twitter photo Here's how to quickly expand these indicators with global internet visibility:
1. Banner hash - fingerprints the unique HTTP server response details.
Hosts linked by this hash:
payconig-betaling[.]one
luxtrust-info[.]xyz
www.luxtrust-info[.]xyz
www.payconig-betaling[.]one Here's how to quickly expand these indicators with global internet visibility:
1. Banner hash - fingerprints the unique HTTP server response details.
Hosts linked by this hash:
payconig-betaling[.]one
luxtrust-info[.]xyz
www.luxtrust-info[.]xyz
www.payconig-betaling[.]one](https://pbs.twimg.com/media/GWGqeh2WEAAdyv7.jpg)

![Michael Koczwara (@michalkoczwara) on Twitter photo Interesting Cobalt Strike C2 impersonating NASA gov.
🥷20.42.96.49 (0/94 VT)
self-signed certificate
🔐/C=US, ST=TX, L=Houston, O=NASA, OU=Engineering, CN=nasa[.]gov Interesting Cobalt Strike C2 impersonating NASA gov.
🥷20.42.96.49 (0/94 VT)
self-signed certificate
🔐/C=US, ST=TX, L=Houston, O=NASA, OU=Engineering, CN=nasa[.]gov](https://pbs.twimg.com/media/GWuVUkpWIAAc8vR.jpg)
![Michael Koczwara (@michalkoczwara) on Twitter photo 🇰🇵Lazarus (APT38) is impersonating Metaschool (Edu platform for Web3 developers)
/metaschool[.]video-meets[.]online
virustotal.com/gui/domain/met… 🇰🇵Lazarus (APT38) is impersonating Metaschool (Edu platform for Web3 developers)
/metaschool[.]video-meets[.]online
virustotal.com/gui/domain/met…](https://pbs.twimg.com/media/GXD61FXWwAAeX-v.jpg)

