Security Trybe
@SecurityTrybe
A Platform For Cyber Security| Networking | Tech| Education|IG-https://t.co/iWeuXqOxRk
ID:1495166759862784000
19-02-2022 22:43:39
17,1K Tweets
165,8K Followers
106 Following
Follow People

Security Trybe Zero Trust Architecture (ZTA) is a security framework that assumes all users and devices, inside or outside an organization, are potential threats. It requires verification and authentication for every access request, enforcing LPA and encryption.




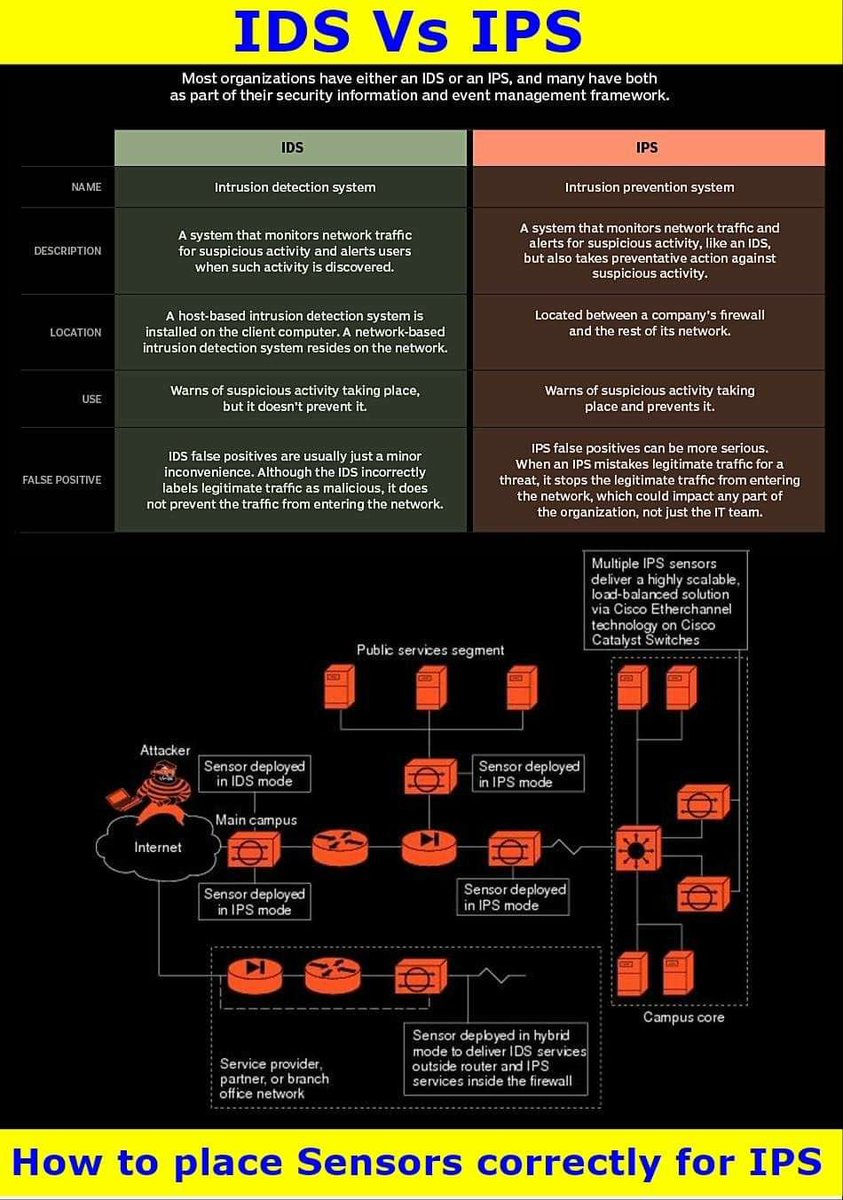
Security Trybe IPS is a device that inspects, detects, classifies and proactively prevents harmful traffic.

Security Trybe MFA- it's more than one way of authorizing a person. Just making sure you are who you say you are. Using passwords, Google authenticator, sms messages etc for authenicating to a platform instead of the traditional username and password only.

Security Trybe SIEM is used by SOC Analysts for monitoring and detection. They store logs from various devices or sources for viewing, correlation, normalization from a central pane of glass. Instead of monitoring one by one from various devices, incident response can be done easily from the…

Security Trybe IDS and IPS are similar. IPS detects and blocks malicious activity while IDS will only alert you upon detection.

Security Trybe CIA - Confidentiality is the protection of your data from 'public knowledge'. Integrity is keeping your data from being altered or modified.
Availability is the act of making sure your data is not stolen or leaked and is always available upon need of demand.



Security Trybe PIIs are personal identifiable informations eg FullName, phone number, email address, IP address etc.
These are informations to infer an individual's identity.
We also have SPII.


Security Trybe 🔐 CIA in Cybersecurity:
- C: Confidentiality keeps secrets safe with encryption.
- I: Integrity ensures data is accurate and tamper-proof.
- A: Availability keeps systems up and running, no matter what.
Defend your digital kingdom with the CIA triad! #Cybersecurity

Security Trybe Skills will get you the job but certs, experience and degrees will get you interviews