JonD
@_jond
Hacking//
ID: 23432954
09-03-2009 13:14:24
2,2K Tweet
1,1K Followers
4,4K Following







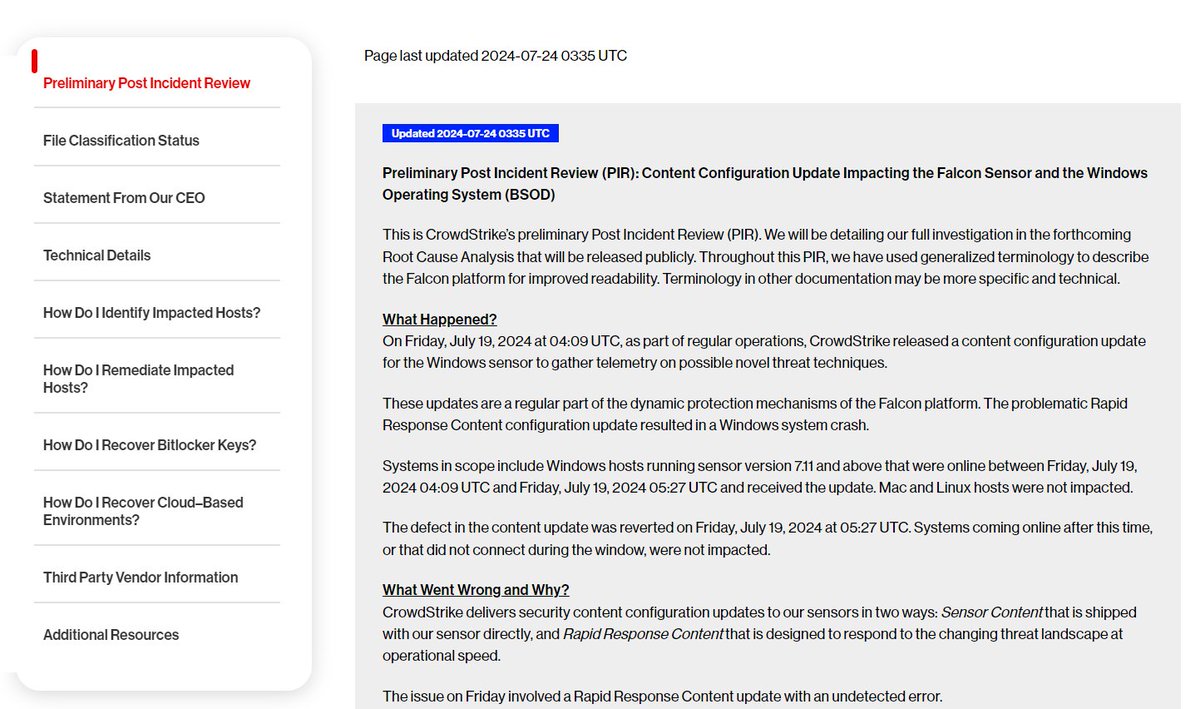
Are we *sure* the CrowdStrike crash wasn't deliberate? They pushed a file full of NULL bytes to their agents which caused the BSoD...






.DuckDuckGo should offer an option to exclude Cloudflare websites from search results for The Tor Project users.