
RootMoksha Labs
@rootmoksha
Cybersecurity focussed Bitcoin venture studio
ID: 1721857998941761536
https://rootmoksha.com/ 07-11-2023 11:51:59
985 Tweet
6,6K Followers
1 Following



P1 Vulnerability in 60 seconds by Wh11teW0lf Link: infosecwriteups.com/p1-vulnerabili… #bugbountytips #BugBounty






Add the folder 'home/000~ROOT~000/' to your wordlist, and you might discover some juicy data. Credits:Karim Habeeb #bugbountytips #BugBounty



Waf block any "</" Try HTML injection </a> worked... </a<script>alert(document.cookie</script> BOOM Credits: Mr. KaLi🇧🇩 #bugbountytips #BugBounty


Finding of this day IDOR in cookie, when I change ID it's take me directly to another user account Browser Extension for cookie: chromewebstore.google.com/detail/cookie-… By:🇸🇦 ROOD | GOAT #bugbountytips #bugbounty


Nmap Cheat sheet Source : github.com/Ignitetechnolo… Credits: Hacking Articles #bugbounty #bugbountytips



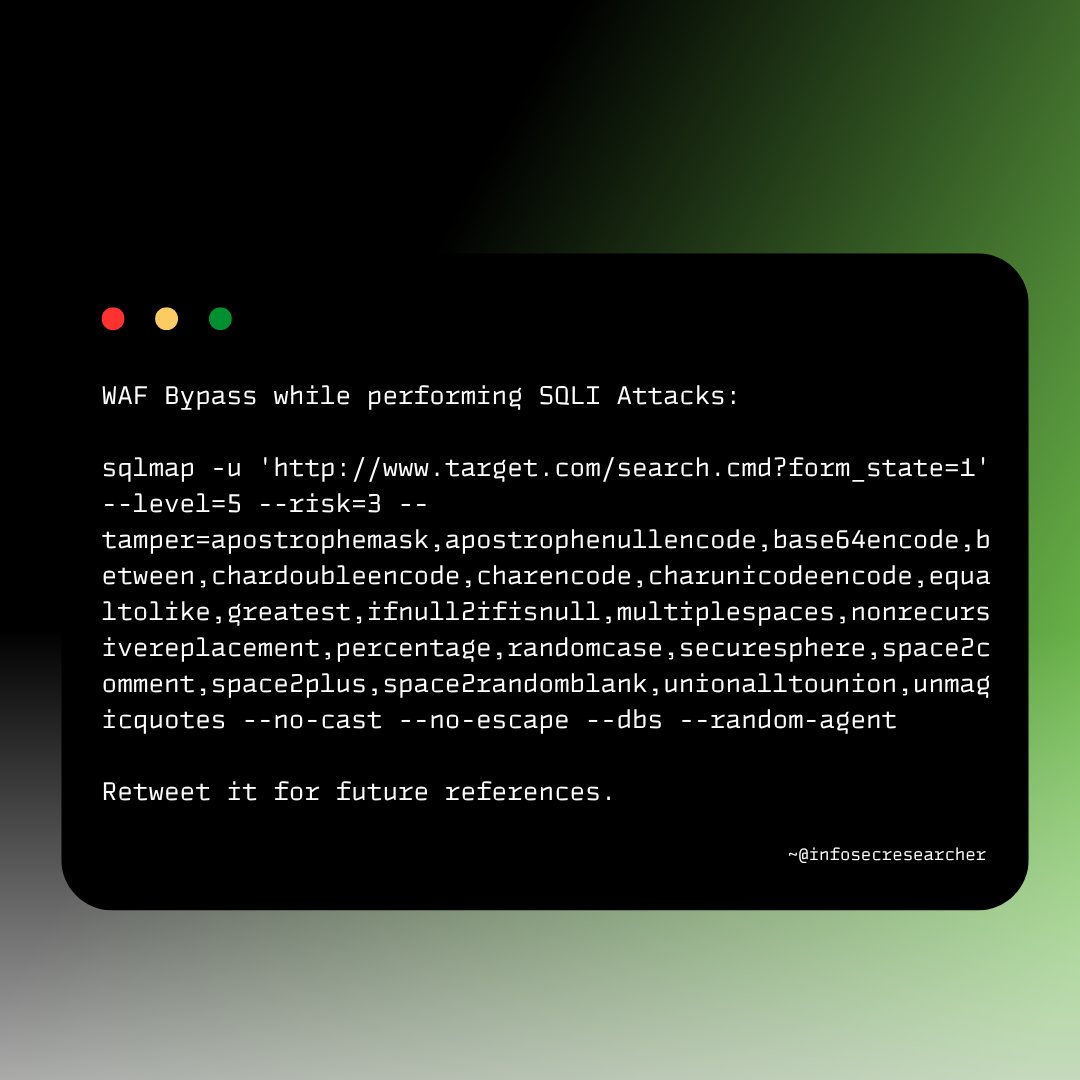
WAF Bypass while performing SQLI Attacks Credits:Fardeen A. #bugbountytips #bugbounty



CRLF vulnerabilities but is a firewall standing in your way? don't forget that sometimes some odd encodings may allow you to bypass firewalls! Credit:Md Ismail Šojal #bugbountytips #bugbounty



Account Takeover via Password Reset poisoning... If changing the Host header or X-Forwarded header doesn't worked, try to add another Host header with the -:space:- Credit - Danial Halo #bugbounty #bugbountytips




![RootMoksha Labs (@rootmoksha) on Twitter photo 𝗗𝗼𝗿𝗸 𝘁𝗼 𝗳𝗶𝗻𝗱 𝗻𝗲𝘄 𝗥𝗼𝗼𝘁 𝗗𝗼𝗺𝗮𝗶𝗻𝘀
𝗗𝗼𝗿𝗸: © [COMPANY_NAME]. All rights reserved.
Credits: <a href="/thecybertix/">Cybertix</a>
#BugBounty #bugbountytips 𝗗𝗼𝗿𝗸 𝘁𝗼 𝗳𝗶𝗻𝗱 𝗻𝗲𝘄 𝗥𝗼𝗼𝘁 𝗗𝗼𝗺𝗮𝗶𝗻𝘀
𝗗𝗼𝗿𝗸: © [COMPANY_NAME]. All rights reserved.
Credits: <a href="/thecybertix/">Cybertix</a>
#BugBounty #bugbountytips](https://pbs.twimg.com/media/GVmI6ItXgAE5_14.jpg)





