Vitali Kremez
@vk_intel
Ethical Hacker | Reverse Engineer | CEO @AdvIntel | Malware Course Author "Zero2Hero" / "Zero2Automated" | Former .gov Cybercrime | Threat Seeker Award
ID: 3332934374
https://vkremez.com 25-08-2015 03:03:37
4,4K Tweet
45,45K Followers
90 Following


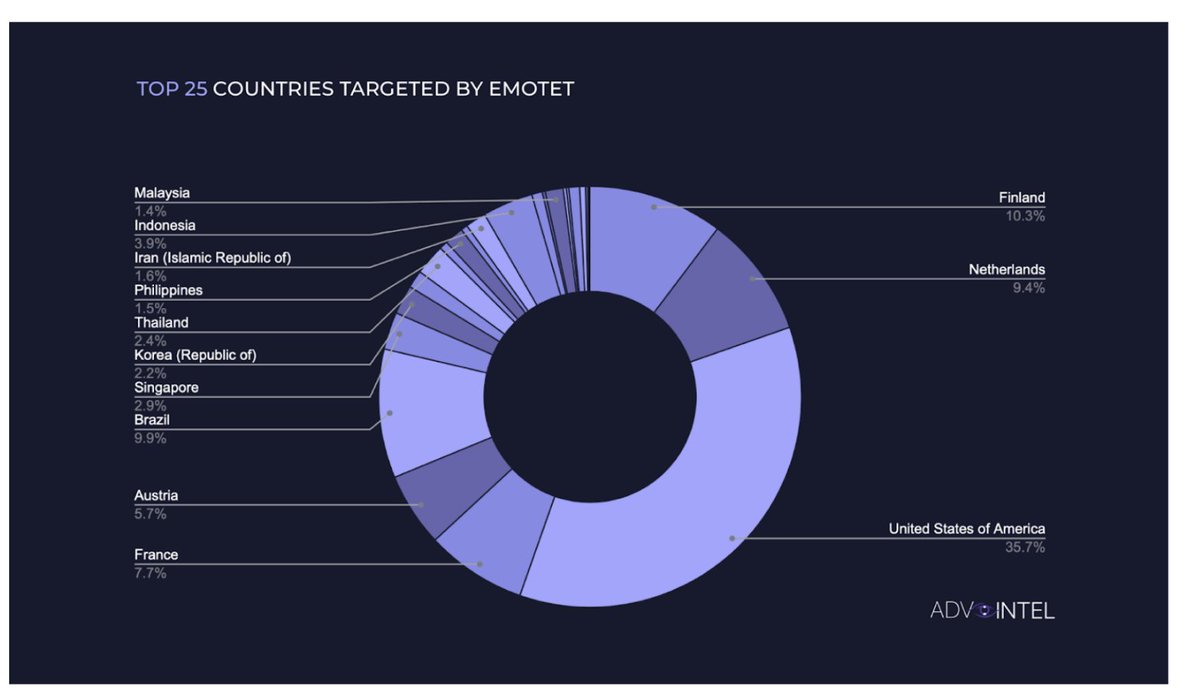
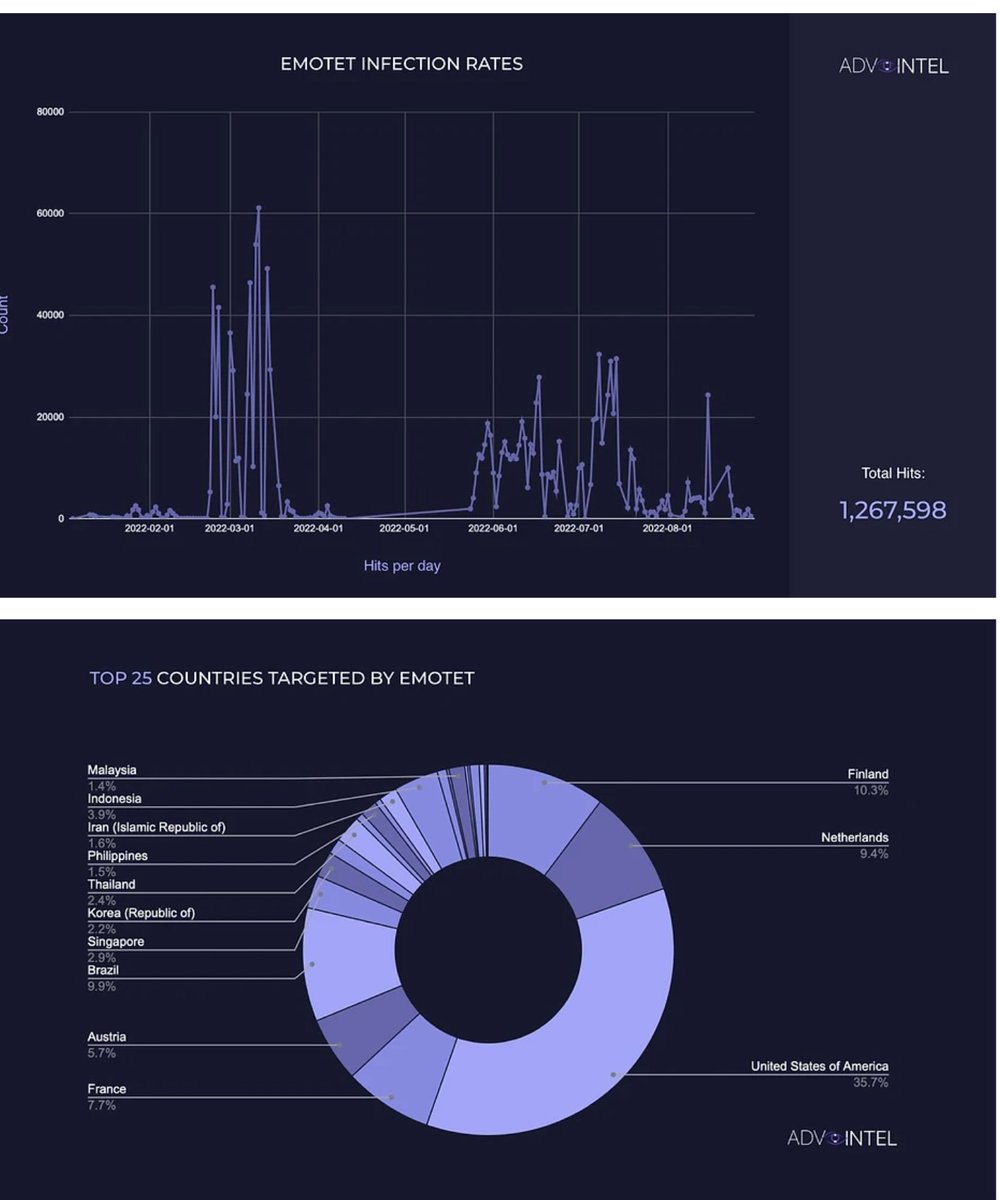
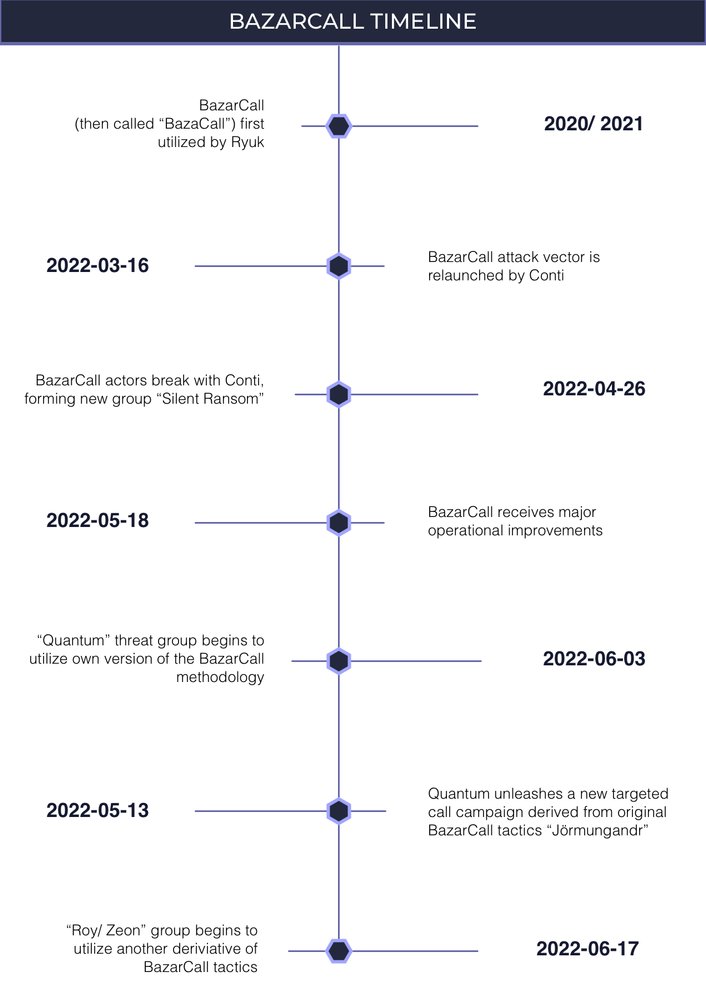
Advanced Intel's Vitali Kremez has published a BazarCall advisory. The “BazarCall” style attack, or call back phishing, is an attack vector that utilizes targeted phishing methodology and first emerged in 2020/2021 as a tool of Ryuk (later rebranded Conti). advintel.io/post/bazarcall…


We're publishing so much great stuff in coming days. There's another Between Two Nerds episode with Tom Uren and thaddeus e. grugq, plus Catalin Cimpanu interviews Vitali Kremez about his call that Ransomware as a Service is dying. Risky Biz News RSS risky.biz/subscribe



Ionut Ilascu Someone is hitting Cobalt Strike servers used by former members of the Conti ransomware gang with messages urging to stop Russia's war: “Stop the war!” “15000+ dead Russian soldiers!” “Be a Russian patriot!” "Stop Putin!"


The Week in Ransomware - September 9th 2022 - Schools under fire - Lawrence Abrams bleepingcomputer.com/news/security/…


The Week in Ransomware - September 16th 2022 - Iranian Sanctions - Lawrence Abrams bleepingcomputer.com/news/security/…


New Royal Ransomware emerges in multi-million dollar attacks - Lawrence Abrams bleepingcomputer.com/news/security/…


The Week in Ransomware - October 21st 2022 - Stop the Presses - Lawrence Abrams bleepingcomputer.com/news/security/…