Zuber
@0bin_Cyber
Cybersecurity/ML • Junior Security Analyst • Pentesting • Malware RE • Threat Hunting • DevOps • Science • History • Fitness - Alxamdulillah!
ID:1245095998990540801
https://localhost.com 31-03-2020 21:10:08
7,2K Tweets
1,2K Followers
335 Following



New Hacking Humble Bundle Bundle Giveaway! I'm going to give away 2 bundles. 18 Books including covering topics like...
👽Practical Malware Analysis
👾Bug Bounties
🕸️Hacking Web API's
🛜Securing Networks
🪟Windows Hacking
🐍Python for Pentesters
To win:
🔁Retweet this tweet
🗣️Say…




Learn Linux Faster with These For Free
Linux basics for hackers OccupytheWeb
THM Linux fundamentals rooms tryhackme.com/module/linux-f…
Linux Journey - (it teaches you in’s and out about Linux / everything) linuxjourney.com
OverTheWire (Bandit CTF) overthewire.org/wargames/bandi…






Day 46 of Networking Basics for Hacker by OccupytheWeb book.
Chapter 14 - SCADA/ICS Networks
* SCADA Manufactures
* SCADA/ISC Communication Protocols
* SCADA Security and Vulnerabilities


Day 45 of Networking Basics for Hackers by OccupytheWeb
Chapter 13 - Automobile Networks
* The CAN Protocols
* CAN-UTILS or SocketCAN
* Setting up a Virtual Can Network
* CAN Simulations
* Reverse Engineer a CAN Packet
* Key Fob Hacking
I got stuck on the most part lol
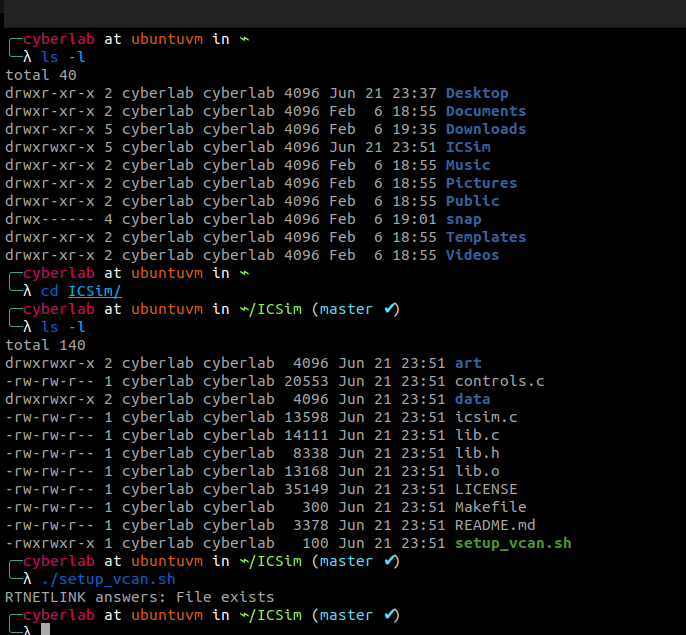

Day 44 of Networking Basics for Hackers by OccupytheWeb
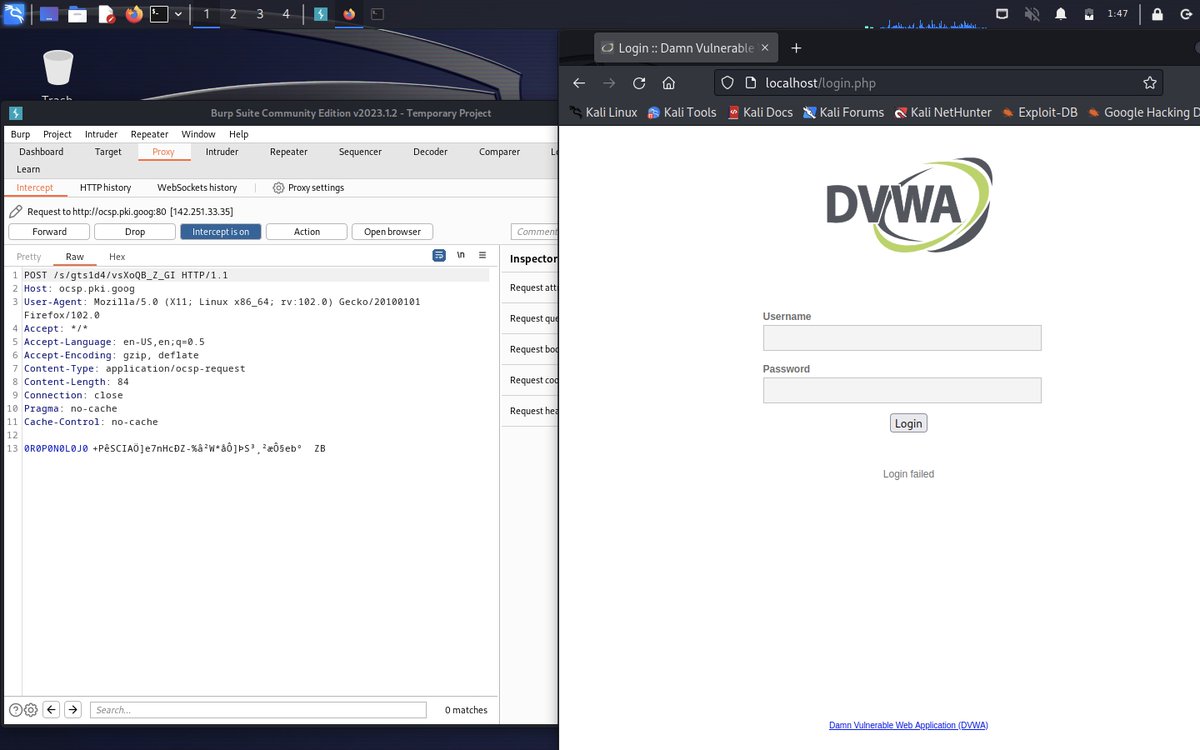
Chapter 12 - The HTTP Protocol.
* HTTP Protocol
* Status Code
* HTTPS
* Pulling DVWA Image using Docker
* Hacking Web App Authentication with BurpSuite