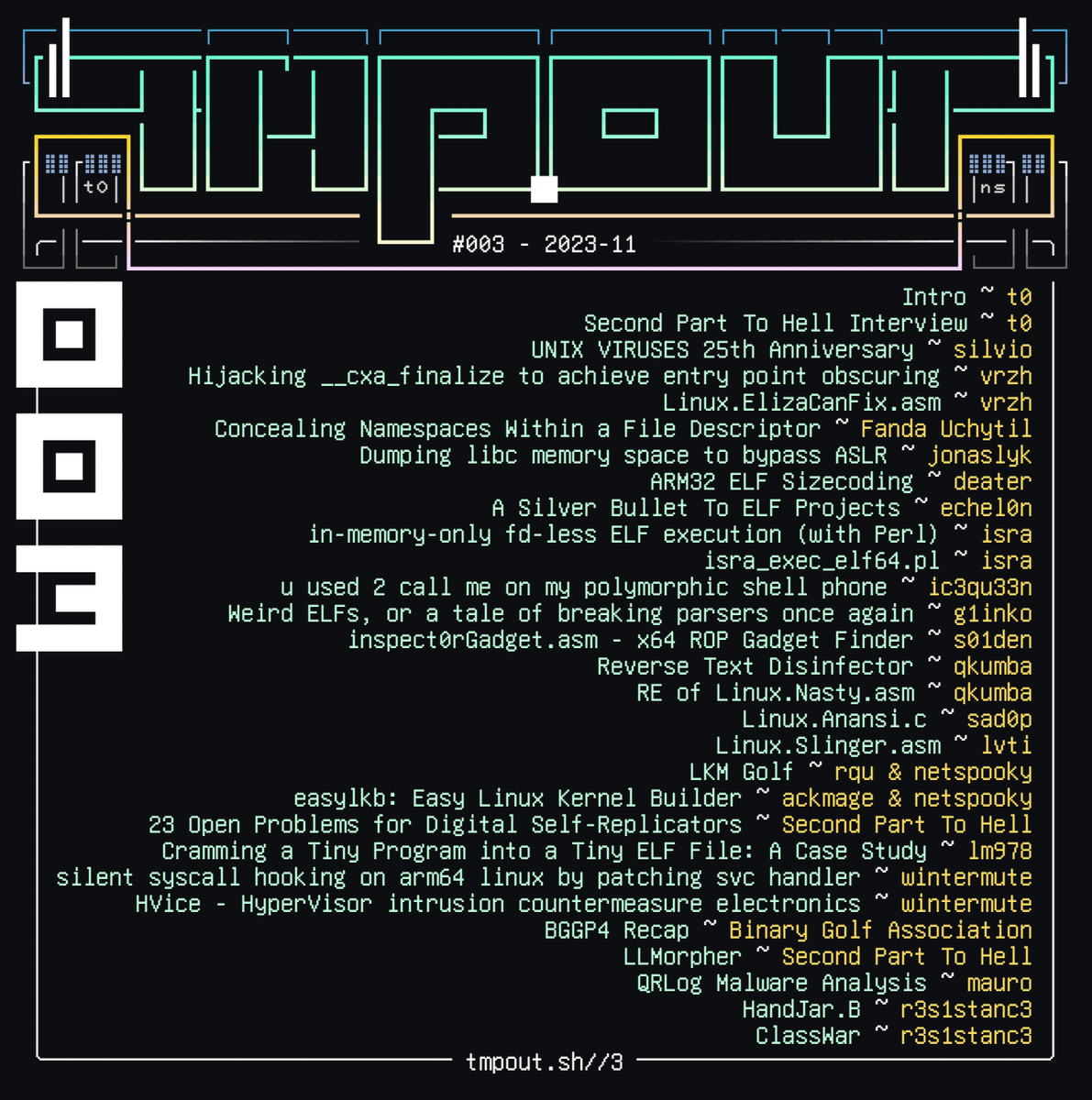
chompie
@chompie1337
hacker + exploit dev @xforce
ID:1179223837742915584
http://chomp.ie 02-10-2019 02:37:35
3,6K Tweets
71,8K Followers
997 Following


hi, check out this tool for easy Linux kernel building and debugging - easylkb
worked on it together with @[email protected]! 💕
writeup: tmpout.sh/3/20.html
repo: github.com/deepseagirl/ea…















You've probably heard a lot of NTLM leaking techniques by now, but have you wondered leaking NTLM info via ports other than 445/SMB? This long-overdue blog post from me reveals an interesting trick which could leak NTLM via any port (e.g. port 80). research.checkpoint.com/2023/abusing-m…