Daniel Heinsen
@hotnops
doin thangs @specterops
ID: 1237387084899516416
https://github.com/hotnops/ 10-03-2020 14:38:12
257 Tweet
1,1K Followers
305 Following



👀 AWS OIDC Provider Enumeration Rami McCarthy built a PoC that enumerates AWS account IDs that have the GitHub Actions OIDC provider configured, leveraging the known_aws_accounts repository → Identified 34 accounts across 29 vendors ramimac.me/oidc-provider-…


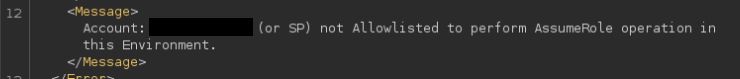
Session Takeover via Pass the Challenge powered by Evan McBroom's lsa-whisperer and Oliver Lyak's impacket fork.










PSA: Apeman exposes a Neo4J panel under the hood. Here is a query to detect roles that are vulnerable to the Amplify vulnerabilities that Nick Frichette presented at Blackhat. Gist here: gist.github.com/hotnops/a1d4ab…