Jared Atkinson
@jaredcatkinson
| Chief Strategist @specterops | Host @dcpthepodcast | Ex PowerShell MVP | USAF Vet | FC Bayern Supporter | Language Learner 🇳🇴 🇮🇹 🇧🇷 |
ID:1608740100
https://posts.specterops.io/on-detection/home 20-07-2013 18:13:53
6,6K Tweet
10,1K Takipçi
1,5K Takip Edilen


So surreal to finally have a copy in my hands. What a journey this has been. Thank you to everyone at No Starch Press who made this a reality.


A special #FF today. Really wanted to highlight the amazing work being done by the teams SpecterOps 🇺🇦 Binary Defense TrustedSec Elastic Security Labs Splunk
They've been dropping some amazing and next level knowledge on us all year long. Just go follow everyone working there tbh and…

BloodHound & BloodHound Enterprise, albeit serving different purposes, are used to secure Active Directory based on the advanced science of graphs & trees. Irshad Ajmal Ahmed explains how these tools work without the complex #cybersecurity jargon. ⬇️


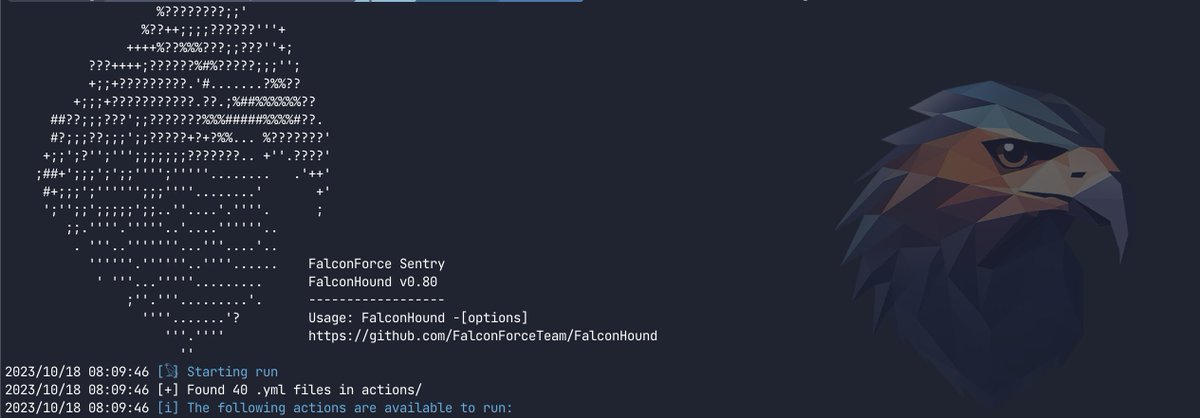
It is out! FalconHound is now public.
github.com/FalconForceTea…
A blue team multi-tool. It allows you to utilize and enhance the power of BloodHound in a more automated fashion
Yesterday I spoke about FalconHound Wild West Hackin' Fest, slides to the talk:
github.com/olafhartong/Pr…

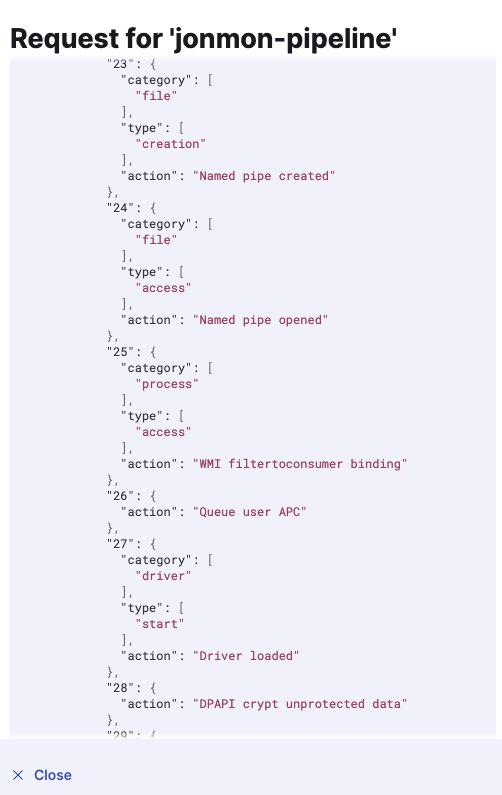
I forgot I started this Jonny Johnson. Super easy to ingest jonmon into elastic.
I even started building an ingest pipeline for it as well, to make it more compatible with other endpoint sources.

Don't forget to check out Justin Kohler on a recent Snake Oiler edition of the Patrick Gray discussing BloodHound Enterprise.
🎧: ghst.ly/3P8XSVe



Later this week, we FalconForce Official will release FalconHound at Wild West Hackin' Fest , a blue team multi-tool. It allows you to utilize and enhance the power of BloodHound in a more automated fashion. Co-developed with Walter.Legowski and Gijs H. Will post the link once its out!