
Rob Fuller
@mubix
Dad / Husband / Marine / Student / Teacher / IAM, Red Team, CTI Director / @Hak5 / @NoVAHackers / @SiliconHBO / @NationalCCDC / @MARFORCYBER Auxiliary
ID:797840
https://malicious.link 27-02-2007 11:22:20
33,2K Tweets
81,4K Followers
26,2K Following
Follow People









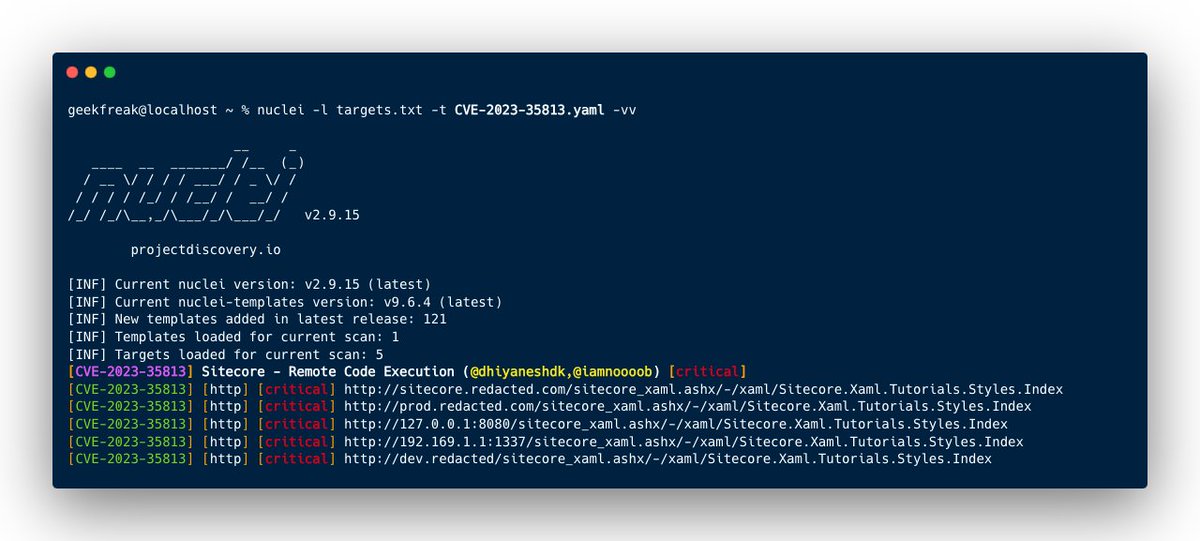
🚨CVE-2023-35813 - Sitecore Remote Code Execution
discovered by CODE WHITE GmbH
CVSS Score - 9.8 | Severity : Critical
Nuclei Template : templates.nuclei.sh/public/CVE-202…
Reference: code-white.com/blog/exploitin…
#bugbounty #cve 2023 #sitecore #hackwithautomation #pdteam #cve




NOLAsec died from COVID. Instead of fighting over the corpse, let live NOLAhackers. Modeled after NoVA Hackers we’re going to have technical cybersecurity meetups in New Orleans










