Boris Larin
@oct0xor
Former console hacker (PS3/PS4). Hunting in the wild 0-days at Kaspersky GReAT. All tweets are my own.
ID:349306056
https://github.com/oct0xor/presentations 05-08-2011 22:10:22
626 Tweet
11,1K Takipçi
469 Takip Edilen


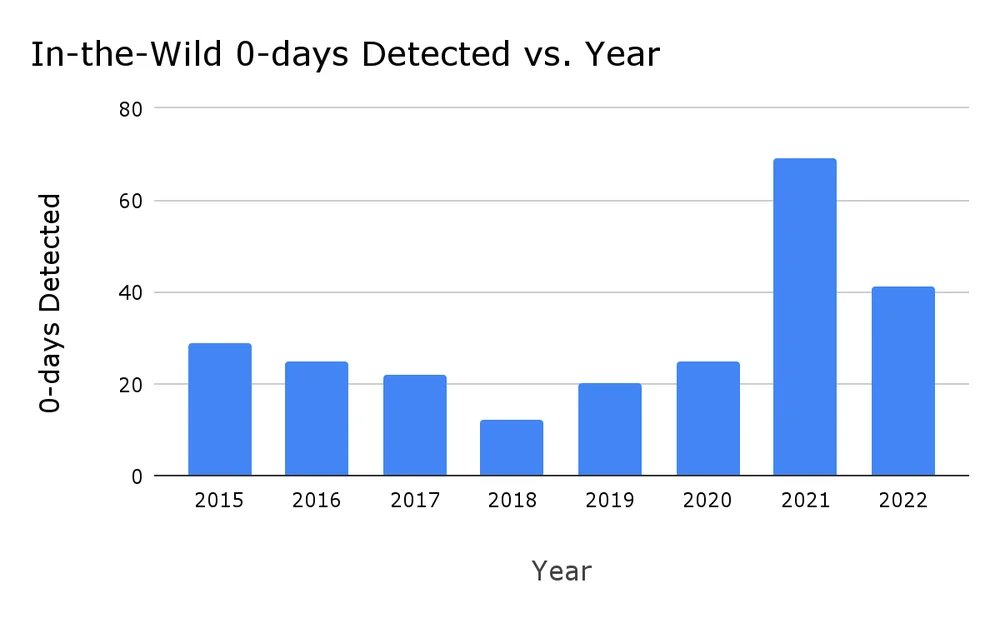
Google's 2022 Year in Review of in-the-wild 0-days is out! 4 key takeaways:
🤖N-days function like 0-days on Android
⚡️0-clicks and new browser mitigations drive down browser 0-days
👯Over 40% of itw 0-days are variants
💥Bug collisions are high
#itw0days
security.googleblog.com/2023/07/the-up…

The story of the #iOSTriangulation in-the-wild 0-days continues! CVE-2023-38606 is another kernel vulnerability that was used in the 0-click exploit chain. Discovered by Valentin Pashkov, Mikhail Vinogradov, Georgy Kucherin, Leonid Bezvershenko, and yours truly. Update all your Apple devices!


🎯Vlad Stolyarov clem1, Bahare, and I from Google TAG, discovered two new in-the-wild 0-days that were patched today: CVE-2023-36874 and CVE-2023-36884. Big thanks to Microsoft for the quick turn around on patches! 👏🏽 #itw0days
msrc.microsoft.com/update-guide/v…
msrc.microsoft.com/update-guide/v…


Today Apple released updates for CVE-2023-32434 (Kernel) and CVE-2023-32435 (WebKit) in-the-wild zero-days which were discovered by us (Georgy Kucherin, Leonid Bezvershenko and yours truly) in the #iOSTriangulation attacks. Update your iOS/iPadOS/macOS/watchOS now!


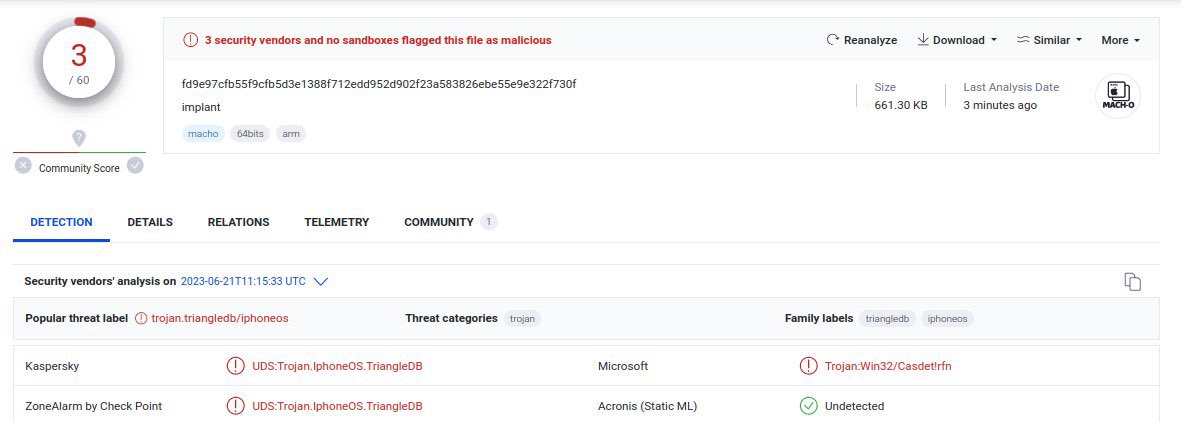
Have you wanted to take your own look at the #iOSTriangulation spyware? Well, we uploaded the #TriangleDB implant to VirusTotal: virustotal.com/gui/file/fd9e9…

Our next blogpost on #iOSTriangulation (securelist.com/triangledb-tri…) is finally out. Today we are ready to share details about the final payload used in the attack, which is a #spyware implant that we dubbed #TriangleDB Leonid Bezvershenko Igor Kuznetsov [1/3]


Insightful thread from Bill Marczak about the #Triangulation campaign from Kaspersky.
Our own hunting has found related domains back to 2018, including in English, Spanish, Portuguese and Chinese. Likely many more targets out there.. Will we see more targets come public?



Boris Larin Thanks so much for letting us know Boris Larin. We've updated the acknowledgement and will fix the bug that caused this miss. We appreciate your partnership to help secure customers.