REhints
@REhints
sharing reverse engineering knowledge
ID:1410020438
https://github.com/rehints 07-05-2013 11:25:24
3,3K Tweet
12,9K Takipçi
5 Takip Edilen


Clang isn't a toolsmith's compiler. PASTA tries to fix this by providing safe-to-use C++ and Python wrappers to the Clang AST. PASTA also answers questions that Clang can't, like how parsed tokens relate back to macro expansions and files. Learn more: blog.trailofbits.com/2023/07/28/the…

#Cartographer : A #Ghidra plugin for mapping out code coverage data. Aka #Lighthouse for Ghidra.
research.nccgroup.com/2023/07/20/too…

📢 #LABScon23 keynote-day speaker announcement!
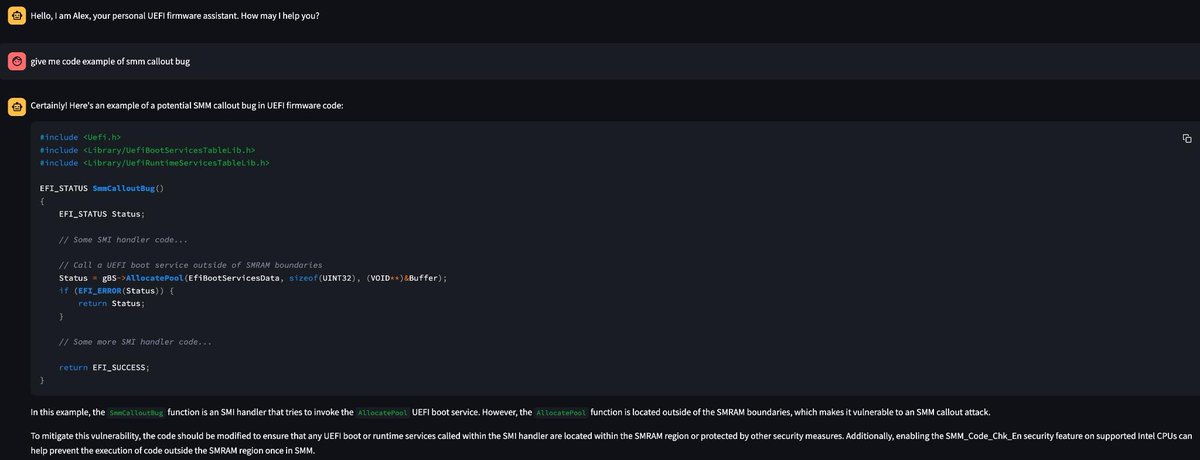
- Binarly's Alex Matrosov (Alex Matrosov) to present research into the potential use of speculative attacks against the System Management Mode (SMM) on AMD-based devices and the methodologies used in the investigation.…

The speculative execution bugs like #Zenbleed are not rare and break confidential computing by design. We have been working with device vendors for over a year to fix #FirmwareBleed /CVE-2022-38087.
Stay tuned for new AMD-specific REsearch at #LABScon23 !
binarly.io/advisories/BRL…


My research on the thing I cannot talk about for another two weeks is nominated for the Pwnie Award 'Most Innovative Research'.
Dark Reading Pwnie Awards - Noms are closed!
darkreading.com/edge/meet-the-…